By adopting these innovative solutions, we can foster a more secure and trustworthy digital ecosystem, ensuring that the benefits of geolocation services are enjoyed without compromising personal data. An easy way to geolocate an IP address is to use an online geolocation database like Geolocation DB. It stores an impressive database of IP addresses obtained from Internet service providers.
The address helps to identify each device in the network and allows communicating with other devices in the network. The network ID represents the network while the host ID represents the host. There are two IP addressing types as classful and classless addressing. Most VPN services will use static IP addresses because it’s easier to connect to an online service when an IP address doesn’t change.
How to wake-on-LAN through VPN router
We use a variety of internal tools to verify IP address location. We also share an IP to geolocation location extended database that provides confidence radius information data to help make educated decisions. From pinging the IP address from those servers, we can sort the results by average scores in ascending order (low to high) to find the lowest ping time. It is easy to artificially slow down Official Login Link connections, but fast connections are harder to produce over long distances, so this is a reliable indicator of physical proximity.
- This feature allows a computer or other network-connected device to be turned on from a sleeping or powered-off state.
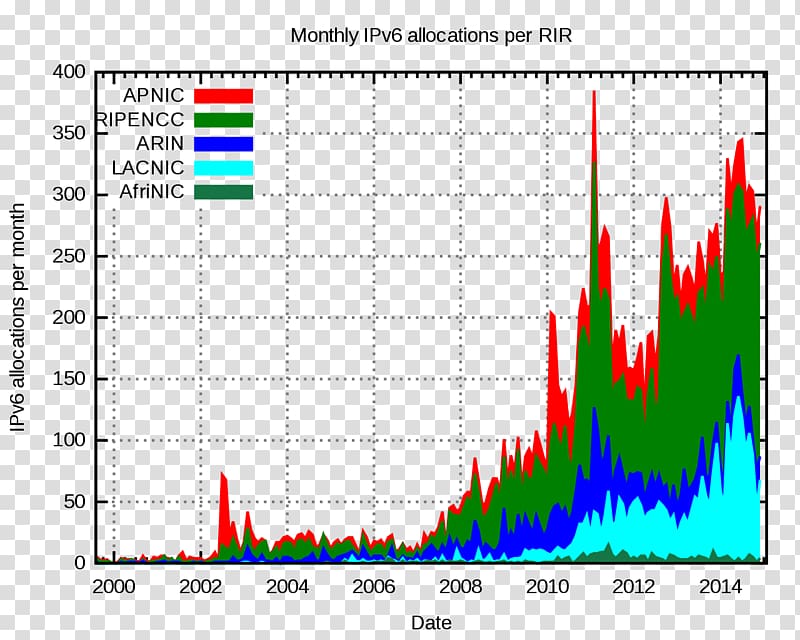
- The distribution of the devices is controlled by RIPE to achieve an even coverage across the IP address space(autonomous systems).
- A condition, either permit or deny, is provided by each rule or line in an access list.
- Bostinnovation.com is there to save your time on the internet by providing you with the details of all the latest happenings across the globe.
- While this data can enhance user experience, it also poses some risks.
Its primary role is to establish, manage, and terminate connections for data transmission while guaranteeing data arrives swiftly and in the correct order. Devices on an Ethernet network use what’s known as a MAC address, sometimes referred to as an Ethernet address. This layer is a protocol layer responsible for the transfer of data between neighboring network nodes. Transport layer breaks the message (data) into small units so that they are handled more efficiently by the network layer. Using a process called “store and forward,” SMTP moves your email on and across networks. It works closely with something called the Mail Transfer Agent (MTA) to send your communication to the right computer and email inbox.
Guide to Attribute-Based Access Control
However, while these services offer convenient features, they also raise concerns about privacy and data security. As shown, this information can reveal real world locations (in addition to civic addresses), elements of an individual’s online activity and possibly lifestyle preferences. In addition to making you a target for ads, geotracking can put you at physical risk.
Network Fundamentals
This is a particular type of VLAN in which frames are not tagged. Bridging loops are more dangerous than routing loops because, as mentioned before, a Layer 3 packet contains a special field called TTL (Time to Live) that decrements as it passes through Layer 3 devices. In a routing loop, the TTL field will reach 0 and the packet will be discarded. A Layer 2 frame that is looping will stop only when a switch interface is shut down. Devices connected to a switch port are in the same collision domains, while devices connected to different ports are in different collision domains. The most important feature of a switch is separating collision domains.